Following such media reports, one can get the wrong impression that almost without exception, large companies are the constant target of cybercriminals. This is very wrong. It is true that the larger the company / institution / organization, or the greater its exposure, the more it becomes a coveted target of criminals, but this only applies to some of them. Namely, a huge part of the so-called hacker attacks happens to small and medium enterprises! This trend is growing worldwide, for a number of reasons. For example, hackers expect (and unfortunately are often right) that smaller companies do not have the resources or awareness of the value of their data, so they take almost no measures to protect it. Another reason is that because large corporations have entire teams dedicated to the prevention and protection against cyber-incidents, it takes a lot of technical knowledge, and almost always - teamwork, in order to successfully break through the system of such an organization, while small and medium enterprises usually do not even have dedicated ICT staff in their ranks, not to mention ICT staff in charge of security!
However, not everything is so grim. While it is true that defending against a large, well-organized attack is almost impossible, especially when it comes to small and medium-sized enterprises, organizations and institutions, this does not mean that we should give up immediately. At the end of the day, even organizing such a large-scale cyber-attack involves resources of criminals as well - and they are more likely to spend them trying to make more money. So, in most cases, it is enough for small and medium enterprises to take a few simple (and relatively cheap) steps in order to significantly increase their resistance to attacks, at least when it comes to "everyday" criminals, who often work alone.
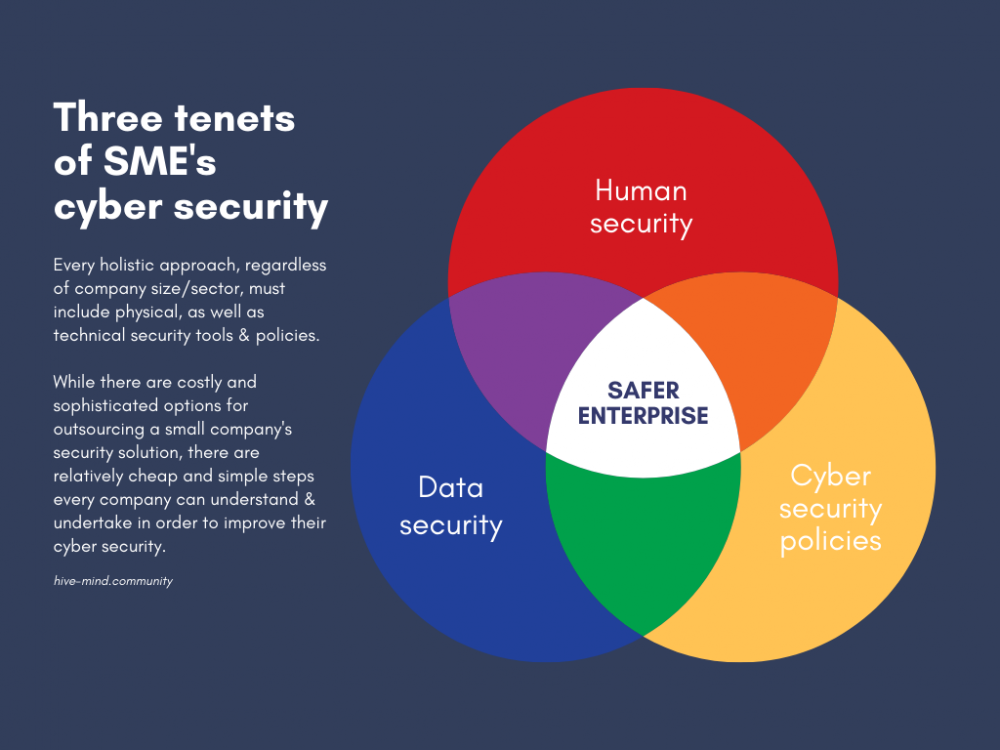
Here are three key points, or postulates, that, if your company addresses them properly, will have a significantly higher level of cyber security, enough to deter and prevent a number of outside attacks.
Employee training
The most important thing at the beginning - the human factor. Company employees are usually the weakest link when it comes to a company's cyber security, and this applies to almost all types and sizes of companies and organizations - the more people on the team, the greater the risk of data leakage, or external attack, or breach. What large companies, such as banks, do very well is take care of their employees' levels of knowledge of data integrity and device security.
Corporations spend huge amounts of money on training all their employees. Of course, not everyone gets the same training, nor is there a need for it. Depending on the level of exposure and knowledge of each individual, a good training program will ensure that everyone is properly acquainted with the basic (and more advanced) topics of cyber security and data integrity. In addition, through regular social engineering prevention training (usually once a year, depending on the company) we make sure that our employees are always up to date with the latest information they need to know in this area, thus securing the future of the company.
It is expected that small and medium enterprises cannot afford to devote so much time only to cyber security training, but with a little creativity and energy of management, mini-trainings can be designed as part of other activities of the company, or a special communication channel can be opened where cyber security topics will be discussed. This will help raise the awareness of all employees (including management) about the importance of protecting and preventing cyber-attacks, as well as the possible consequences for everyone in the company.
Another way to work regularly on employee "training" is to have a regular meeting or exchange of information dedicated to safety. This can also be incorporated with other similar training programs, such as first aid, occupational safety, and others. Promoting good practices, such as cyber hygiene, to every employee will dramatically improve the resilience of the entire company. Regular exchange of credible information, especially from trusted sources and relevant to the industry in which your company operates, will help to timely detect cyber-attack trends in companies similar to yours, giving you time to prepare.
Data security – data integrity and backups
The security of the data that your company operates on a daily basis is vital. Without them, the work will simply stop completely. Data such as bank accounts, passwords for access to confidential documents, contact information of your clients, partners, etc. - are data that are of great value, and this is known to malicious actors. So, in order to secure the future of the company, we must take care of this data, which is often data about us, but also about our customers, making sure it has an appropriate level of protection.
One of the simplest ways you can accomplish this is to back up your data regularly. With this, even in the event of an incident, we will always have the opportunity to restore the old data and our business to continue to function, without spending large sums of money on paying the hackers (which does not guarantee the data in its entirety anyway).
In addition to making regular backups of data, another good practice is to ensure that each team member has adequate access to the data he / she needs for the job. For example, setting levels of authorized access to more sensitive data only to certain individuals, rather than to the entire company, would reduce the "window" for possible external hacking. Also, providing multi-factor authentication to all employees, and regularly changing passwords (including the alarm system and front door!) will dramatically contribute to greater security of premises and user accounts - and ensure greater data integrity. If certain employees (e.g. management) need to regularly connect to unsafe networks outside the workplace, for example when traveling, it is worth considering the mandatory use of VPN on their devices.
We have to be very careful with the data we work with every day, and without which we could not function. One unauthorized approach is enough to crash our entire operation, and even with the recovery of some of the lost data, what will never restore is our (self)confidence in the systems, and our reputation with the clients we have worked with.
Cyber security policies
Crowning all the efforts, energy and finances invested in the preparation of your company from cyber threats would be most appropriate through the establishment of the so-called cyber security policies. With updated, implemented and monitored policies, the security of the whole company will be at a solid level - far better than most other small and medium enterprises.
Good policies will ensure, inter alia, that in the event of an incident, the entire procedure before, during, and after the incident will be noted and available for future study. This is not much different from other workplace incidents, such as fire, flood, theft and the like. In all cases, a thorough analysis of the reasons why the incident occurred, how it went (course), and how it ended is necessary. Only by regularly following metrics, and in the context of cyber security, can we be sure that our policies work and protect us, and modify those that do not.
An example of a relatively simple policy that will significantly help boost a company's cybersecurity is the so-called "clean desk" policy or a clean desktop. In short, this policy aims to establish order in the context of what can, must, and must not be found on the desk of every employee at any point. Among other things, such a policy can include a rule for not writing passwords to access computers on a piece of paper, which is then pasted on the edge of the keyboard or monitor. Also, in the drawers of the desks, you must not store keys from other offices or auxiliary rooms. Additionally, in such a policy it is good to include a rule not to leave removable media (USB sticks, etc.) in apparent places, where they could be easily and quickly stolen.
Another useful policy is the policy of regularly changing user account passwords for all employees. E-mail accounts are usually the first on the list for regularly changing passwords, but we must not forget the others: e.g. official company social media profiles, business laptop and phone passwords, etc. In such a policy, there may be a rule to change the Wi-Fi password in the office, at certain intervals, in order to prevent unauthorized access to the Internet network used by all employees. In addition, it is relatively easy to open a so-called “guest” network, which will be intended exclusively for occasional visitors to the company's premises, and in this way there will be no need to share the password with anyone interested.
There are a number of cybersecurity policies that, if regularly updated, successfully implemented (meaning all employees are aware of their importance and regularly practice them), and monitored, i.e. followed by appropriate metrics for their performance, can significantly improve the cyber security of a company, organization or institution. However, cybersecurity policies, like workplace safety, personal data protection, and any other, can only work if everyone agrees that they are important, necessary, and adhered to. Which brings us back to step 1, that is, the human factor in cyber security.
Tech protection can really protect us a lot - but it can often be expensive and unsustainable for smaller businesses. In addition, external technical protection cannot guarantee 100% security, and anyone who tries to "sell" this to you - is not telling the truth. Without a proper change in company culture about the importance of data, and regular, relevant information, as well as clear, effective and holistic cybersecurity policies, it is only a matter of time before the next cyber incident "surprises" you.
If you'd like to find out more about ways to take care of your organisation's Cyber Security, check out this blog post with the Operational Security Best Practices Guide written by Radically Open Security and a webinar with their co-founder, a TEDx speaker and Expert on Digital Security, Melanie Rieback.
Background illustration: Photo by Artem from Adobe Stock / Adobe Stock license